SOAR with SNORT and Elastic Stack
What is SOAR
As someone who hosts his things online, the presence of exploit bot roaming free on the internet is a daily threat. Handling and keeping track on incoming exploit atteempts of publicly available servers has been a luscious tasks for enterprieses who have online presence (which as this time is almost all of them). The enterpries who do care bout their data, turn into the market of cyber security. Most of the solutions available are highly sophisticated softawre or intergratede devices who turn into the front line of the data protection. These things will do all the dirty job, most important of all Detection and Response on security threats.
SOAR (Security Orchestration, Automation, and Response) is a swiss army knive for security events handling. SOAR its self is a stack of softwares that enable organization to perform data collection and response on security threats without human assistance. Such products are Splunk Phantom, IBM Resilient and FortiSOAR
Motang SOAR
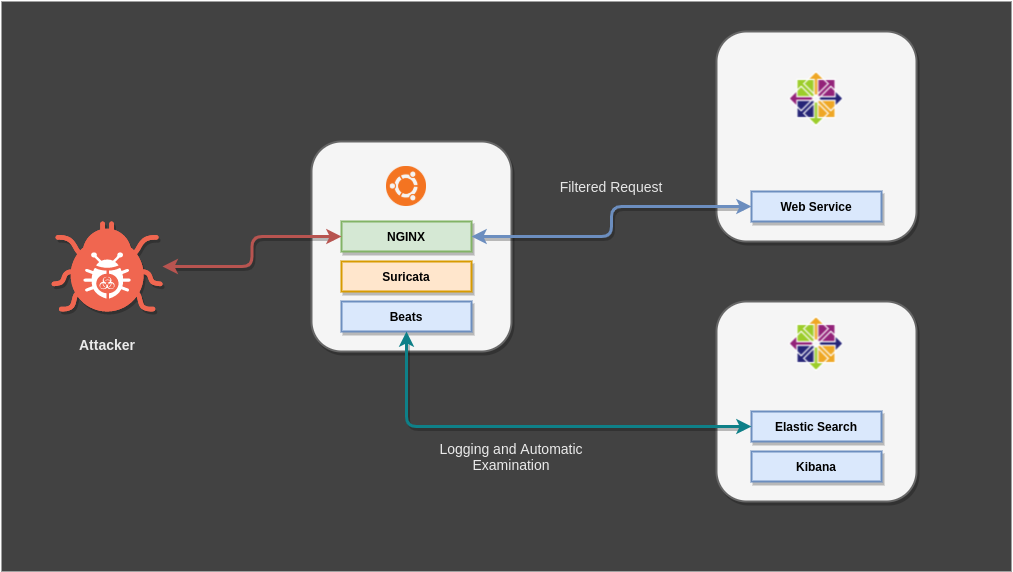
Motang SOAR is my latest attempt to implement SOAR functionalities using only open source software. How it turned out even surpass my own expectations. All of this deployment performed on centos 8 as monitoring node, and ubuntu 20.04 as end node.
Software Stack
Elastic Stack : Logging and Monitoring
elasticsearch as the main core of our logging and management stack, kibana as the dashboard for monitoring and mangament of all the implemented rules, and beats as the data logger on the end node where the IDS/IPS were placed.
Suricata : IDS & IPS
Suricata is a opensource intrusion detection and prevention engine. In this deployment we use EmergingThreat set of rules which covers almost all the bot attacks that will happen on your server.
NGINX : Proxy Server
In this deployment we only exposed our end node to the internet, using nginx we can redirect the incoming traffic into the right system.
Deployment Architecture